2 min read
Meet INCOSE's Guide to Writing Requirements With AI Quality Checker Webinar
Don't feel like reading? Watch the webinar recording instead! In systems engineering and project management, the importance of clear and precise...
3 min read
SPEC Innovations Team
:
1/24/24 2:27 PM

Not in the mood for reading? Watch the video instead!
In today's digital landscape, where news of successful cyber attacks is a daily occurrence, the need for robust cybersecurity strategies is more critical than ever. In this blog, we will delve into the intricacies of designing a cyber risk management strategy, with a focus on the best practice known as "Cybersecurity by Design." Additionally, we will explore the primary benefits of Innoslate, a powerful tool that aids in the implementation of effective cybersecurity measures.
Our system of interest is the modern digital enterprise, characterized as a large-scale complex system of systems. The use case under consideration is the design of a cyber risk management strategy, particularly emphasizing the Security by Design approach. In this scenario, imagine a board of directors tasking the CEO with updating them on the efforts to manage cyber risks. This involves collaboration with functional team leaders, external resources, threat intelligence sources, and cyber supply chain representatives.
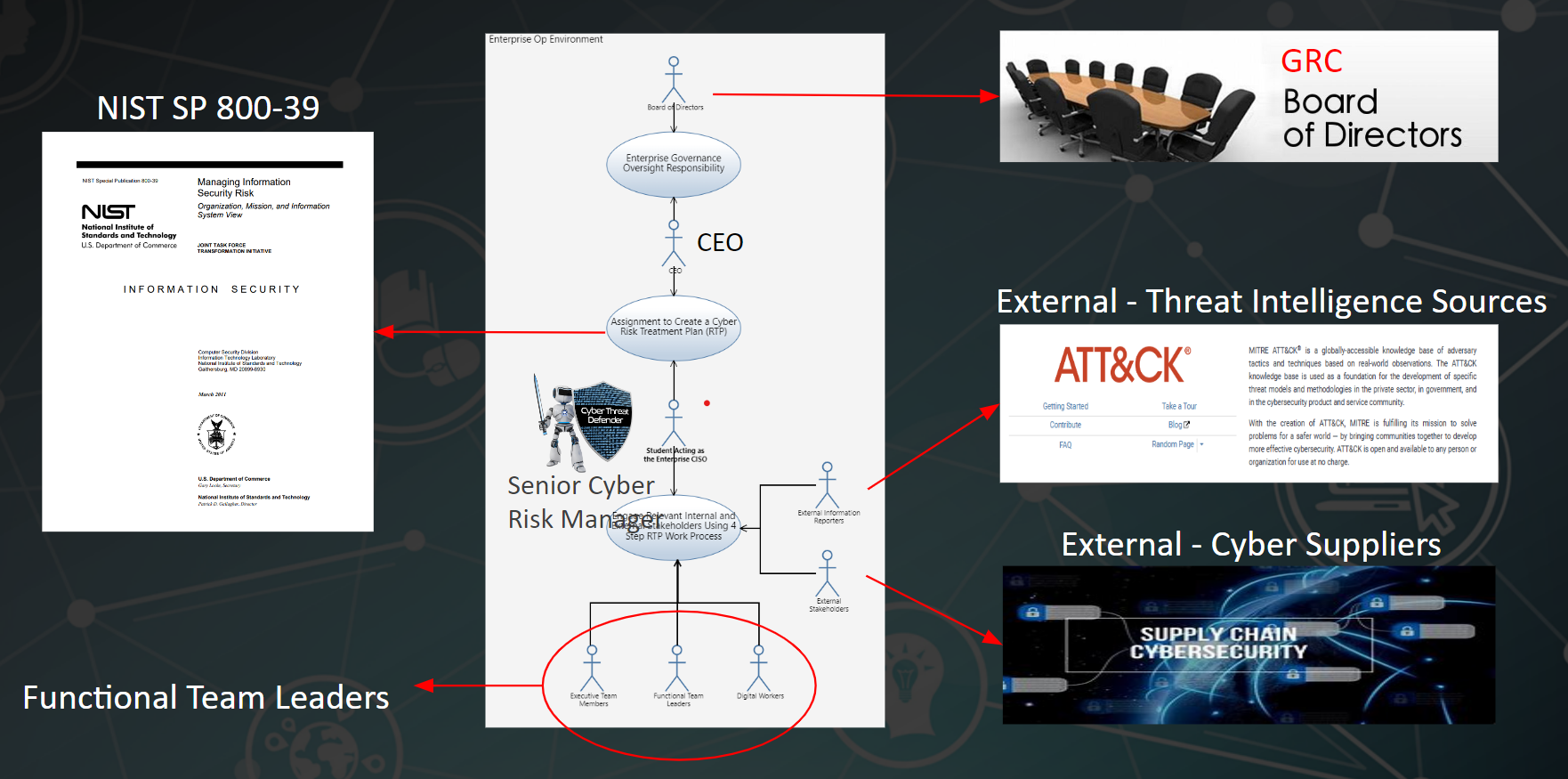
*Innoslate's SysML Use Case Diagram Used in Image
Cybersecurity by Design is not a new concept; it has been around and gaining traction over the years. The methodology involves strengthening the cybersecurity of a system from the very start of its design and architecture. Unlike an afterthought or add-on, security becomes an integral part of the system's lifecycle. The goal is to reasonably protect against malicious threat actors gaining access to devices, data, and connected systems.
To design an effective cyber risk management strategy, one must consider various elements. The strategy should conform to established guidance, such as NIST SP 800-39, addressing both strategic and tactical cyber risks. Strategic risks arise when an enterprise's cybersecurity program is insufficient for security objective achievement, while tactical risks occur during successful cyber attacks due to either the absence or failure of security controls.
Innoslate proves to be a valuable tool in this process. Its capability to enumerate project requirements, offer scheduling views, and provide a timeline diagram facilitates efficient project management. The primary benefit of Innoslate is its ability to support persistent team-based cybersecurity operations. Cybersecurity is an ongoing effort, and Innoslate ensures that teams can seamlessly collaborate, share knowledge, and maintain a consistent approach to defend against evolving threats.
Understanding the work process and design method is crucial. The architectural development method helps in cascading requirements through business architecture, information system architecture, and technology architecture. Documenting the design outputs, such as an Enterprise Architecture Security Model, aids in creating a structured and effective security architecture.
Visualizing the Enterprise Attack Surface involves considering multiple elements such as digital technology, cyber supply chain, people, and enterprise operating sites. Innoslate's state machine diagram helps in transitioning from an insecure state to a secure state, continuously monitoring for changes and adapting to potential risks.
Developing a risk treatment plan involves creating a risk register, assessing risks based on likelihood and impact, and implementing controls. Innoslate's security control library assists in mapping controls onto the enterprise attack surface. The game within the game involves optimizing detective and preventive controls based on the available budget.
The landscape of cybersecurity is evolving, with new requirements such as SOC 1 Type 1 and Type 2 reports becoming essential for business operations. SEC compliance reporting further emphasizes the need for public companies to disclose their cybersecurity risk management strategies. This formalization of cybersecurity practices is a response to the growing importance of managing cyber risks in the corporate world.
Understanding the legal landscape of cybersecurity is crucial. In the event of a data breach, having a well-reasoned cyber risk management strategy becomes a defense against negligence claims. Innoslate's database tracing of history and decisions provides evidence needed to respond to legal challenges, demonstrating a commitment to achieving a reasonable professional standard for handling sensitive information.

Innoslate emerges as a feature-rich application empowering enterprises to implement Security By Design. It not only aids in designing effective cybersecurity strategies but also facilitates operationalizing teamwork and knowledge sharing. In the face of a motivated threat actor, speed and decision quality are paramount, and Innoslate proves to be a valuable ally in this ongoing cybersecurity battle.
As organizations continue to navigate the complex cybersecurity landscape, adopting best practices and leveraging tools like Innoslate will be crucial in safeguarding digital enterprises against evolving threats.
Have questions about model-based systems engineering or requirements management? Talk to an expert and see how Innoslate can streamline your projects from start to finish.

2 min read
Don't feel like reading? Watch the webinar recording instead! In systems engineering and project management, the importance of clear and precise...
.png)
Can't read at the moment? Watch the recording instead!

Don't feel like reading? Watch the webinar recording!